am using the -f option here for appending the forward-slash while making a brute-force attack on the target URL.
gobuster dir -u geeksforgeeks.org -w /usr/share/wordlists/dirb/common.txt -f –wildcard
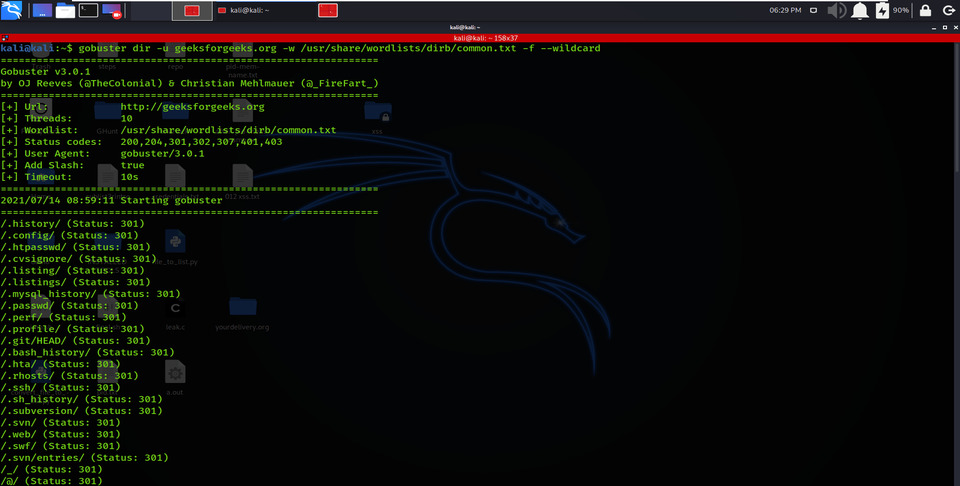
Appending Forward Slash
8. Enumerating Directory with Specific Extension List
There are many scenarios where we need to extract the directories of a specific extension over the victim server, and then we can use the -X parameter of this scan. This parameter allows the file extension name and then explores the given extension files over the victim server or computer.
gobuster dir -u geeksforgeeks.org -w /usr/share/wordlists/dirb/common.txt -x .php –wildcard
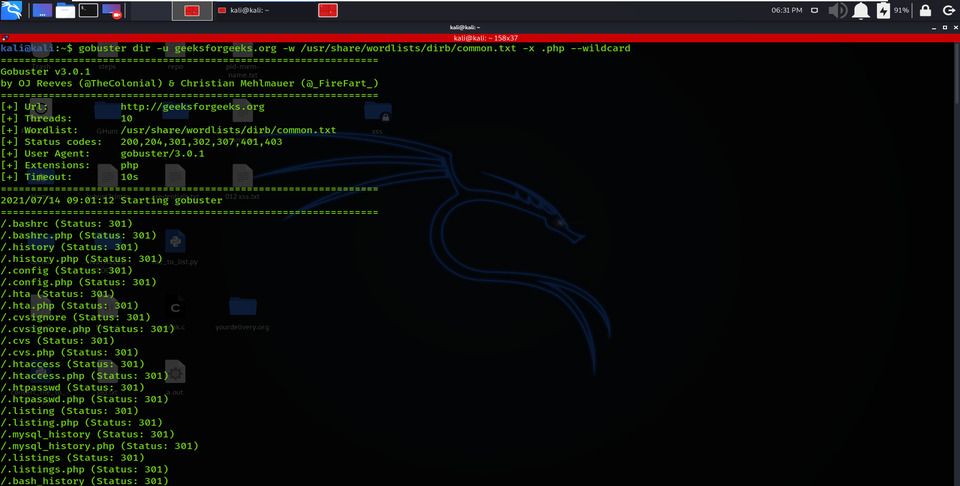
Enumerating Directory with Specific Extension List
9. Follow Redirect
Using -r options allows redirecting the parameters, redirecting HTTP requests to another, and changing the Status code for a directory or file.
gobuster dir -u geeksforgeeks.org -w /usr/share/wordlists/dirb/common.txt -q –wildcard
gobuster dir -u geeksforgeeks.org -r -w /usr/share/wordlists/dirb/common.txt -q –wildcard
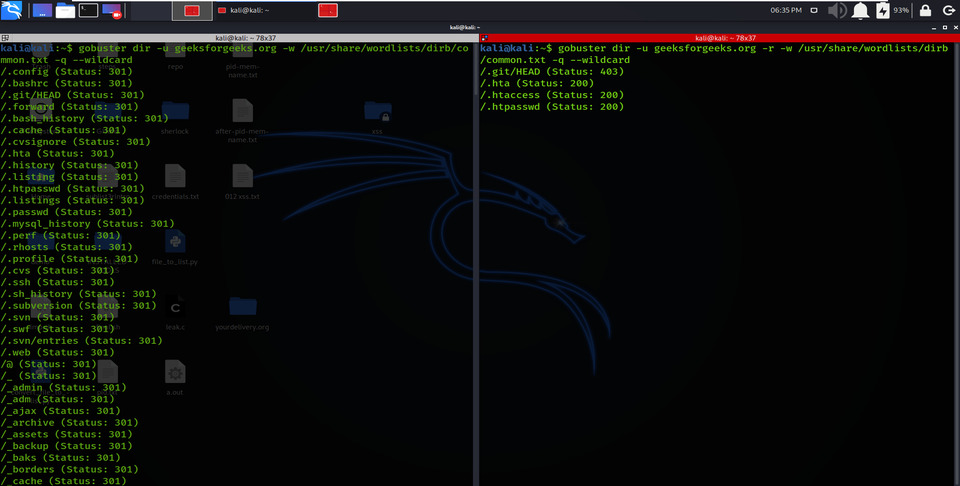
Follow Redirect
10. HTTP AUTHORIZATION (-u username: password)
HTTP Authentication/Authentication mechanisms are all based on the use of 401-status code and WWW-Authenticate response header. The most generally used HTTP authentication mechanisms are Primary. The client sends the user name and password un-encrypted base64 encoded data.
So, to avoid this kind of authentication with the help of Gobuster, we have used the command below:
gobuster dir -u http://testphp.vulnweb.com/login.php -w /usr/share/wordlists/dirb/common.txt -U test -P test –wildcard
gobuster dir -u geeksforgeeks.org -w /usr/share/wordlists/dirb/common.txt -f –wildcard

Appending Forward Slash
8. Enumerating Directory with Specific Extension List
There are many scenarios where we need to extract the directories of a specific extension over the victim server, and then we can use the -X parameter of this scan. This parameter allows the file extension name and then explores the given extension files over the victim server or computer.
gobuster dir -u geeksforgeeks.org -w /usr/share/wordlists/dirb/common.txt -x .php –wildcard

Enumerating Directory with Specific Extension List
9. Follow Redirect
Using -r options allows redirecting the parameters, redirecting HTTP requests to another, and changing the Status code for a directory or file.
gobuster dir -u geeksforgeeks.org -w /usr/share/wordlists/dirb/common.txt -q –wildcard
gobuster dir -u geeksforgeeks.org -r -w /usr/share/wordlists/dirb/common.txt -q –wildcard

Follow Redirect
10. HTTP AUTHORIZATION (-u username: password)
HTTP Authentication/Authentication mechanisms are all based on the use of 401-status code and WWW-Authenticate response header. The most generally used HTTP authentication mechanisms are Primary. The client sends the user name and password un-encrypted base64 encoded data.
So, to avoid this kind of authentication with the help of Gobuster, we have used the command below:
gobuster dir -u http://testphp.vulnweb.com/login.php -w /usr/share/wordlists/dirb/common.txt -U test -P test –wildcard


















