StormWall projects a 170% expansion in DDoS Assaults toward the finish of 2024 and urges organizations to carry out moderation systems.
Driving network safety supplier, StormWall, has delivered a far reaching report on the territory of Dispersed Disavowal of Administration assaults (DDoS assaults) in Q1 2023. The report, in view of an examination of assaults on StormWall's clients across different areas, uncovers a critical increment of 47% in DDoS assaults contrasted with a similar period last year.
The discoveries, imparted to Hackread.com, feature a troubling pattern of botnet use and a developing act of smokescreening to disguise multi-vector assaults.
The review uncovers that aggressors are progressively focusing on basic framework and administrations, including calculated administrations, installment handling centers, and banking frameworks, trying to influence a bigger number of clients. The typical assault strength arrived at a pinnacle of 1.4 Tbps, and the longest assault went on for 4 days.
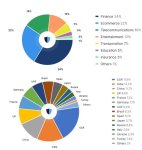
Among the areas focused on, the monetary business encountered the largest number of assaults, representing 34% of the aggregate and seeing a stunning 68% expansion contrasted with Q1 2022. Web based business likewise confronted critical difficulties, getting through 22% of the assaults and encountering a 51% increment from the earlier year. Broadcast communications stayed a well known focus, with 16% of the assaults and a 47% year-over-year increment.
The utilization of botnets in DDoS assaults keeps on getting some decent forward momentum, with more than 38% of assaults utilizing organizations of compromised gadgets. Moreover, the act of smokescreening, where DDoS assaults are utilized as distractions in multi-vector attacks, expanded by 28% contrasted with the earlier year.
The report additionally uncovers that more damaging HTTP assaults are turning out to be progressively open to run. Accordingly, 82.3% of DDoS assaults designated the application layer (L7), while 11.7% were aimed at the vehicle (L4) and network (L3) layers of the OSI model. DNS was focused on in 2.3% of the assaults, and the excess 3.7% were focused on different targets.
Geologically, the US (17.6% assault share), India (14.2%), and China (11.7%) stay the most designated nations. In any case, the Unified Middle Easterner Emirates saw a remarkable flood in assaults, with the extent almost multiplying from 3.8% in Q1 2022 to 6.4% in the ongoing year. Russia and Ukraine, then again, encountered a decrease in DDoS action as hacktivism died down.
Did you had any idea that in 2021, the US and China both stood firm on the footing of being the top nations with the most uncovered cloud servers because of misconfiguration? India positioned fifth in such manner.
StormWall's report stresses the heightening danger of DDoS assaults, as proven by the critical ascent in assault volume, strength, and span. With danger entertainers continually adjusting their strategies and coordinating DDoS assaults inside multi-vector occurrences, associations need to address blackouts from overburdened servers as well as information breaks, ransomware, and other related dangers.
In light of information examination from client-designated assaults, StormWall projects a further 170% increment in DDoS assaults toward the finish of 2023. Considering these disturbing discoveries, the organization unequivocally suggests that all organizations look for proficient DDoS assurance to defend their web-based resources in the impending year.
Driving network safety supplier, StormWall, has delivered a far reaching report on the territory of Dispersed Disavowal of Administration assaults (DDoS assaults) in Q1 2023. The report, in view of an examination of assaults on StormWall's clients across different areas, uncovers a critical increment of 47% in DDoS assaults contrasted with a similar period last year.
The discoveries, imparted to Hackread.com, feature a troubling pattern of botnet use and a developing act of smokescreening to disguise multi-vector assaults.
The review uncovers that aggressors are progressively focusing on basic framework and administrations, including calculated administrations, installment handling centers, and banking frameworks, trying to influence a bigger number of clients. The typical assault strength arrived at a pinnacle of 1.4 Tbps, and the longest assault went on for 4 days.
Among the areas focused on, the monetary business encountered the largest number of assaults, representing 34% of the aggregate and seeing a stunning 68% expansion contrasted with Q1 2022. Web based business likewise confronted critical difficulties, getting through 22% of the assaults and encountering a 51% increment from the earlier year. Broadcast communications stayed a well known focus, with 16% of the assaults and a 47% year-over-year increment.

The utilization of botnets in DDoS assaults keeps on getting some decent forward momentum, with more than 38% of assaults utilizing organizations of compromised gadgets. Moreover, the act of smokescreening, where DDoS assaults are utilized as distractions in multi-vector attacks, expanded by 28% contrasted with the earlier year.
The report additionally uncovers that more damaging HTTP assaults are turning out to be progressively open to run. Accordingly, 82.3% of DDoS assaults designated the application layer (L7), while 11.7% were aimed at the vehicle (L4) and network (L3) layers of the OSI model. DNS was focused on in 2.3% of the assaults, and the excess 3.7% were focused on different targets.
Geologically, the US (17.6% assault share), India (14.2%), and China (11.7%) stay the most designated nations. In any case, the Unified Middle Easterner Emirates saw a remarkable flood in assaults, with the extent almost multiplying from 3.8% in Q1 2022 to 6.4% in the ongoing year. Russia and Ukraine, then again, encountered a decrease in DDoS action as hacktivism died down.
Did you had any idea that in 2021, the US and China both stood firm on the footing of being the top nations with the most uncovered cloud servers because of misconfiguration? India positioned fifth in such manner.
StormWall's report stresses the heightening danger of DDoS assaults, as proven by the critical ascent in assault volume, strength, and span. With danger entertainers continually adjusting their strategies and coordinating DDoS assaults inside multi-vector occurrences, associations need to address blackouts from overburdened servers as well as information breaks, ransomware, and other related dangers.
In light of information examination from client-designated assaults, StormWall projects a further 170% increment in DDoS assaults toward the finish of 2023. Considering these disturbing discoveries, the organization unequivocally suggests that all organizations look for proficient DDoS assurance to defend their web-based resources in the impending year.


















