Hackers mention in a letter about the data breach of Ledger users in December 2020.

Scammers send fake devices to Ledger hardware wallet users to steal cryptocurrency. In a post on Reddit, one of the users told about the received
package , which looks like a Ledger Nano X device . The device is sent in a supposedly branded package with an attached letter. In the letter, the scammers reported that the device was sent to replace the existing one, as information about the user was published on the hacker forum RaidForum.
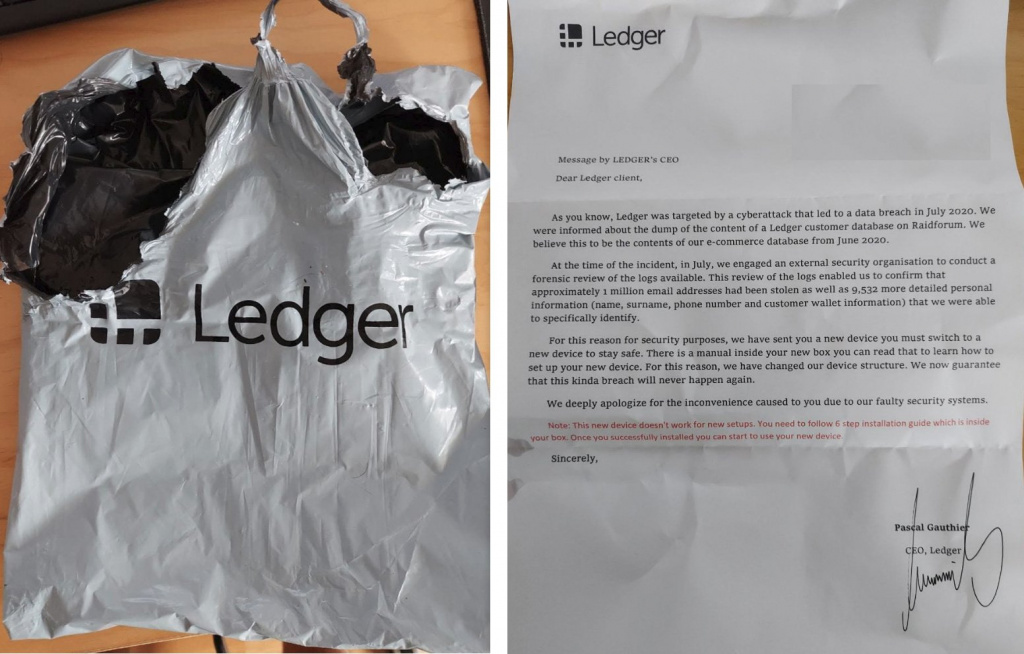
“For this reason, for security reasons, we have sent you a new device, which you must replace the old one with for security reasons. Inside the box is a manual for using the new device. In connection with this incident, we have changed the structure of our device and we guarantee that such a violation will never happen again, ”the letter says.
Interestingly, data on 272,853 Ledger device users were actually published on the RaidForums hacker forum in December 2020. This served as a compelling explanation for the shipment of the new device.
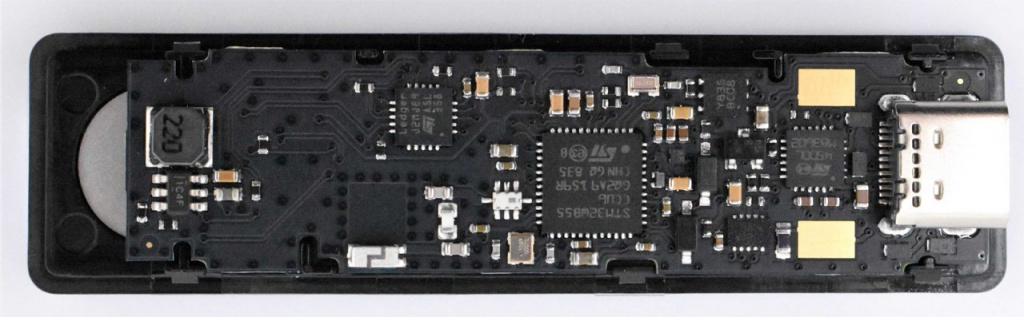
As you can see in the photos, the PCB of the fake Ledger device has been modified. According to information security expert Mike Grover, the attackers added a USB flash drive to the device and connected it to a USB connector.
The accompanying instructions ask the recipient of the parcel to connect the Ledger to their computer, open the disc that appears, and launch the included application. Next, you need to enter the Ledger recovery passphrase (used to generate the private key for a specific wallet) and import the wallet to the new device. After entering the phrase, it is sent to cybercriminals who use it to import the victim's wallet onto their own devices in order to steal the contained funds in the cryptocurrency.

__________________

Scammers send fake devices to Ledger hardware wallet users to steal cryptocurrency. In a post on Reddit, one of the users told about the received
package , which looks like a Ledger Nano X device . The device is sent in a supposedly branded package with an attached letter. In the letter, the scammers reported that the device was sent to replace the existing one, as information about the user was published on the hacker forum RaidForum.

“For this reason, for security reasons, we have sent you a new device, which you must replace the old one with for security reasons. Inside the box is a manual for using the new device. In connection with this incident, we have changed the structure of our device and we guarantee that such a violation will never happen again, ”the letter says.
Interestingly, data on 272,853 Ledger device users were actually published on the RaidForums hacker forum in December 2020. This served as a compelling explanation for the shipment of the new device.
As you can see in the photos, the PCB of the fake Ledger device has been modified. According to information security expert Mike Grover, the attackers added a USB flash drive to the device and connected it to a USB connector.

The accompanying instructions ask the recipient of the parcel to connect the Ledger to their computer, open the disc that appears, and launch the included application. Next, you need to enter the Ledger recovery passphrase (used to generate the private key for a specific wallet) and import the wallet to the new device. After entering the phrase, it is sent to cybercriminals who use it to import the victim's wallet onto their own devices in order to steal the contained funds in the cryptocurrency.

__________________











